Feature #284
closedFeature #235: [Security Audit Round 2 ]
[Security Audit Round 2 ] Clickjacking Attack (Repeated)
0%
Description
Clickjacking Attack (Repeated)
CWE : CWE-1021
Description :
Clickjacking is a malicious technique of tricking a Web user into clicking on something
different from what the user perceives they are clicking on, thus potentially revealing
confidential information or taking control of their computer while clicking on seemingly
innocuous web pages.
Affected Path(s) :
https://earogya.satragroup.in/ *-Applicable to entire application
Impact :
An attacker can host this domain in other evil site by using iframe and if a user fills the
given field it can directly redirect as logs to attacker and after its redirect to your web
server. Leading to steal user information too and use that host site as phishing of your
site its CSRF and Clickjacking.
Evidence/Proof Of Concept :
Step 1: Sample HTML code for Clickjacking.
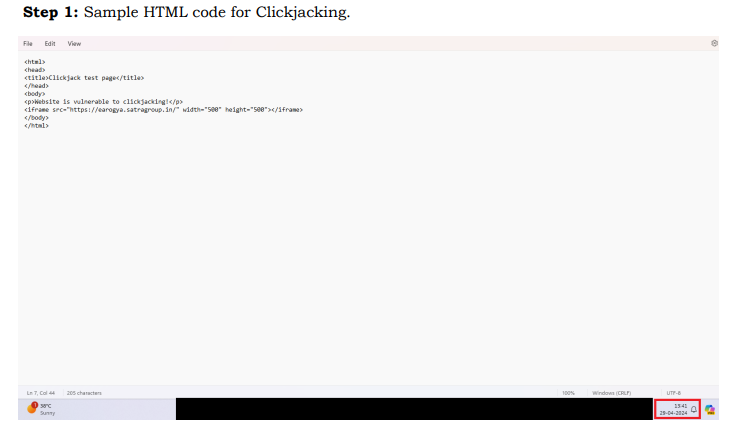
Step 2: Clickjacking attack is successfully executed as shown in the screenshot.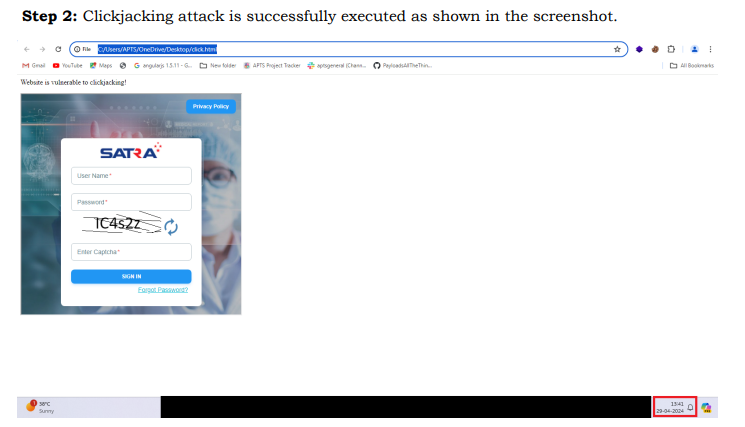
Recommendation :
It is recommended to implement any of the following:
Use the X-FRAME Options header in response headers and set its value to DENY
or Same Origin or ALLOW-FROM a specified URL
Use Content-Security-Policy header and set frame-ancestors attribute to self.
Files