Feature #261
openFeature #235: [Security Audit Round 2 ]
[Security Audit Round 2 ] Application Logic Bypass (Reapeated)
0%
Description
Application Logic Bypass (Repeated)
CWE : CWE-840
Description :
The application does not perform or incorrectly performs an authorization check when
attempts to perform an action.
Affected Path(s) :
https://earogya.satragroup.in/patient/39/patient-Registration *-Applicable to entire
application
Impact :
An attacker could read sensitive data, either by reading the data directly from a data
store that is not properly restricted, or by accessing insufficiently-protected, privileged
functionality to read the data.
Evidence/Proof Of Concept :
Step 1: Patient user registration submitted successfully with wrong date as shown in below
screenshot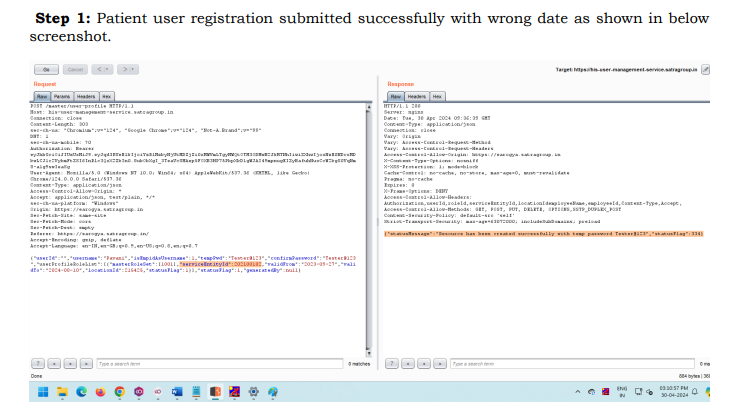
Recommendation :
Make sure that the access control mechanism is enforced correctly at the server side on
every page.
Files