Feature #260
closedFeature #235: [Security Audit Round 2 ]
[Security Audit Round 2 ] OTP Bruteforce (Reapeated)
0%
Description
OTP Bruteforce (Repeated)
CWE : CWE-799
Description :
Application allows users to submit multiple wrong OTPs which lead to bruteforce
attacks to guess the correct OTP.
Affected Path(s) :
https://earogya.satragroup.in/login *-Applicable to entire application
Impact :
Account takeover can be possible by using this vulnerability.
Evidence/Proof Of Concept :
Step 1: Application accepting multiple OTP requests which leads to brute force the OTP by
submitting multiple requests.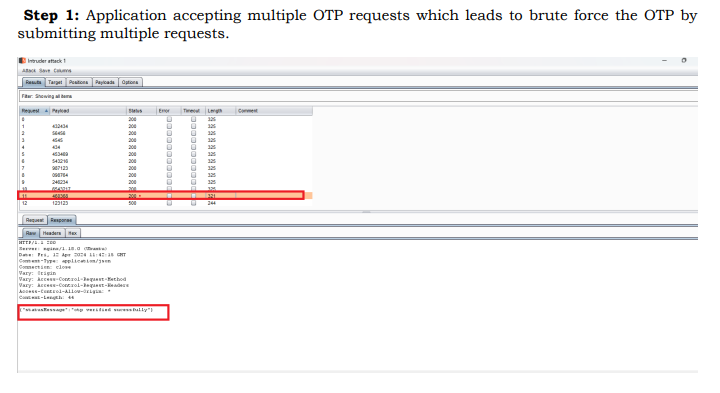
Step 2: Functionalilty issue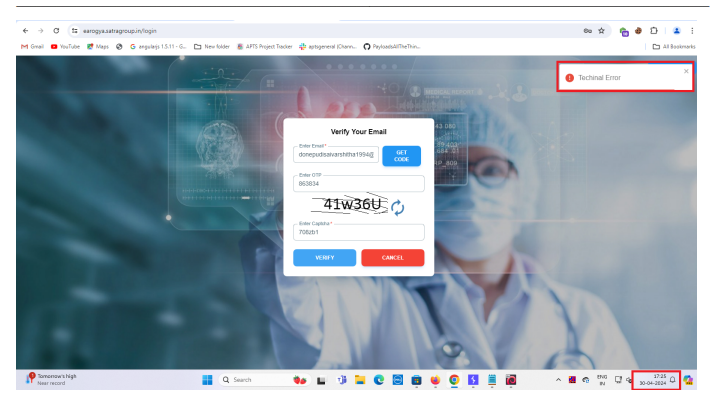
Recommendation :
It is recommended to allow only 3 to 5 wrong attempts of OTPs. After the limit block the
mobile number for some time or provide a new OTP.
Files
Updated by Sivakanth Kesiraju about 1 year ago
- Target version set to Sprint 1 (29th April - 3rd May)
Updated by Sivakanth Kesiraju about 1 year ago
- Target version changed from Sprint 1 (29th April - 3rd May) to Security Audit
Updated by Harish Beechani about 1 year ago
- Status changed from Resolved to Ready for Prod
Updated by Kalyan Battula about 1 year ago
- Status changed from Ready for Prod to Closed
- Assignee changed from Harish Beechani to Kalyan Battula
working fine now not allowing multiple Opt attempts