Feature #254
closedFeature #235: [Security Audit Round 2 ]
[Security Audit Round 2 ] OTP Bypass (Repeated)
0%
Description
OTP Bypass (Repeated)
observation : Repeated
CWE : CWE-287
Description :
In this application OTP is disclosed in response.
Affected Path(s) :
https://earogya.satragroup.in/login *-Applicable to entire application
Impact :
Attacker can us e the OTP value to bypass the login without the actual user intervention
Evidence/Proof Of Concept :
Step 1: Access the application and Go to forgot password page and enter random OTP as
shown in below screenshot.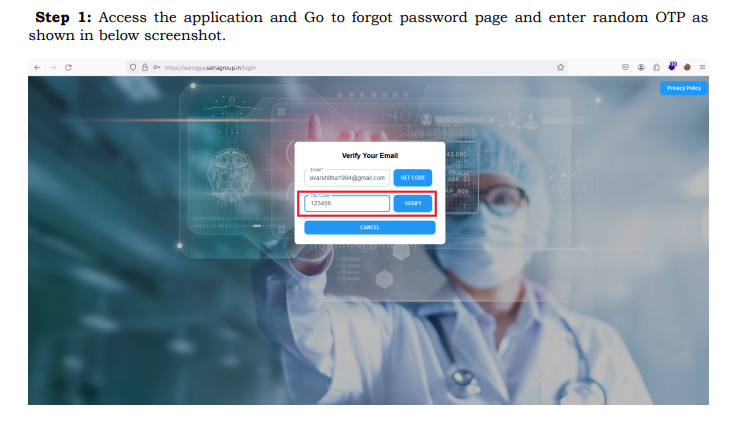
Step 2: Successfully Navigate the password change page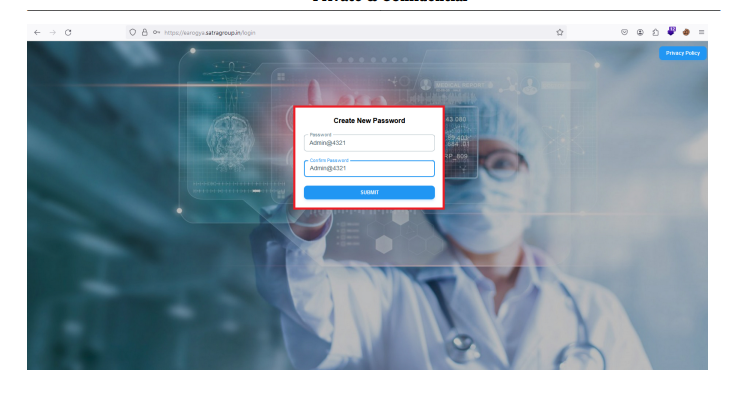
Step 3: Capture the above request and Observe the response.New Password has been
changed successfully even after entering the invalid OTP as shown in below screenshot.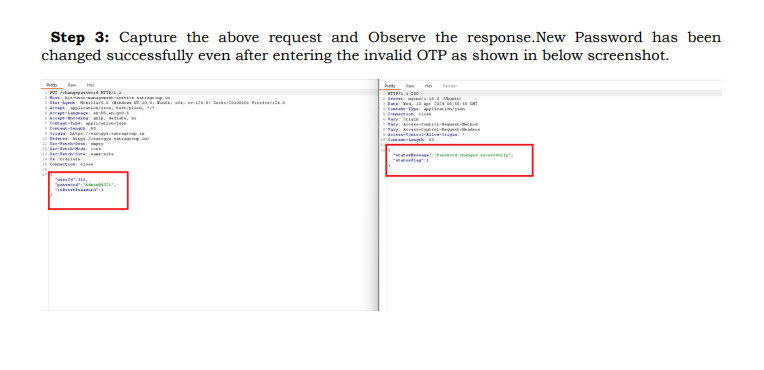
Step 4: Functionality issue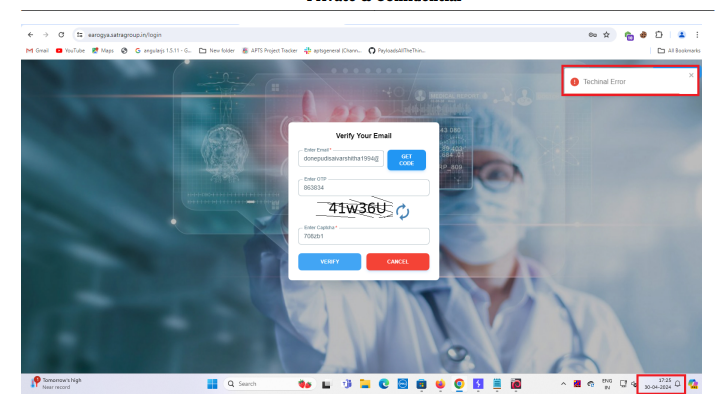
Recommendation :
It is recommended not to disclose the OTP in the response
Files