Feature #278
openFeature #235: [Security Audit Round 2 ]
[Security Audit Round 2 ] Sensitive Data Passed Through URL Parameters (Repeated)
0%
Description
Sensitive Data Passed Through URL Parameters
observation : Repeated
CWE : CWE-598
Description :
The web application uses the HTTP GET method to process a request and includes
sensitive information in the query string of that request.
Affected Path(s) :
https://his-healthidservice.satragroup.in/abdm/isAvailable/customHealthId/srinuks.1 *-Applicable to entire
application
Impact :
This allows attackers to obtain sensitive data such as usernames, passwords, tokens
(authX), database details, and any other potentially sensitive data. Simply using HTTPS
does not resolve this vulnerability.
Evidence/Proof Of Concept :
Step 1: ABHA Username Passed Through URL as shown in below screenshot.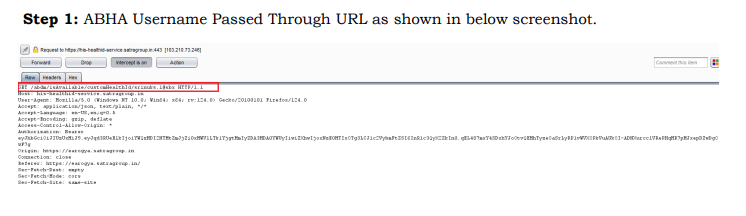
Step 2: Functionality issue
Recommendation :
When sensitive information is sent, use the POST method (e.g. registration form, login
form, etc.).
Files
Updated by Harish Beechani about 1 year ago
- Assignee set to Pavan kumar Siddamsetti
Updated by Sivakanth Kesiraju about 1 year ago
- Target version set to Sprint 1 (29th April - 3rd May)
Updated by Sivakanth Kesiraju about 1 year ago
- Target version changed from Sprint 1 (29th April - 3rd May) to Security Audit
Updated by Harish Beechani about 1 year ago
- Status changed from Resolved to Ready for Prod