Feature #268
openFeature #235: [Security Audit Round 2 ]
[Security Audit Round 2 ] Cross Origin Resource Sharing (CORS) Misconfiguration
0%
Description
Cross Origin Resource Sharing (CORS) Misconfiguration
observation : Repeated
CWE : CWE-642
Description :
The application implements an HTML5 cross-origin resource sharing (CORS) policy for
this request that allows access from any domain.
Affected Path(s) :
/(WebServer)
Impact :
Any website can make XHR requests to your site and access the responses.
Evidence/Proof Of Concept :
Step 1: Cross Origin Resource Sharing (CORS) Misconfiguration as shown in below
screenshot.
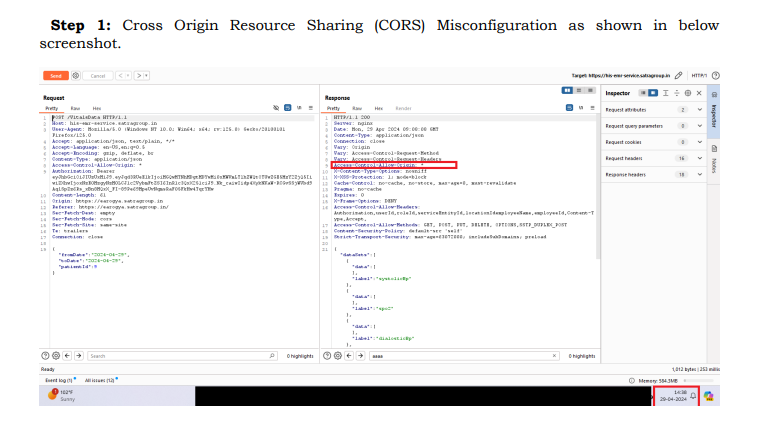
Recommendation :
It is recommended not to use Access-Control-Allow-Origin: *.
Instead use Access-Control-Allow-Origin header should contain the list of
origins that can make CORS requests.
Reference Link:
https://cwe.mitre.org/data/definitions/942.html https://owasp.org/www-community/attacks/CORS_OriginHeaderScrutiny
Files
Updated by Sivakanth Kesiraju about 1 year ago
- Target version set to Sprint 1 (29th April - 3rd May)
Updated by Sivakanth Kesiraju about 1 year ago
- Target version changed from Sprint 1 (29th April - 3rd May) to Security Audit
Updated by Harish Beechani about 1 year ago
- Status changed from Resolved to Ready for Prod